Using the AWS Lambda.NET Core project templates for Visual Studio, you can create a Lambda function using Microsoft.NET Core. For prerequisites and information about setting up the AWS Toolkit for. The AWS Toolkit for Visual Studio (AWS Toolkit) is a plug-in for the Visual Studio IDE that makes it easier for developers to develop, debug, and deploy.NET applications that use Amazon Web Services. Because AWS EC2 is using physical Apple Mac mini machines instead of virtual machines you can get the full OS experience you need for the development of apps. In this blog post I want to show you how easy the setup is and how you get the SAP SDK for iOS installed.
- Aws Toolkit Visual Studio For Mac Osx
- Aws Toolkit For Vs Code
- Aws Tools For Visual Studio
- Aws Toolkit For Visual Studio For Mac
- Aws Toolkit For Visual Studio Code Mac
Coverage:
The AWS Toolkit for Azure DevOps adds tasks to easily enable build and release pipelines in Azure DevOps (formerly VSTS) and Azure DevOps Server (previously known as Team Foundation Server (TFS)) to work with AWS services including Amazon S3, AWS Elastic Beanstalk, AWS CodeDeploy, AWS Lambda, AWS CloudFormation, Amazon Simple Queue Service and Amazon Simple Notification Service, and run commands using the AWS Tools for Windows PowerShell module and the AWS CLI.
The AWS Toolkit for Azure DevOps is available from the Visual Studio Marketplace.
This is an open source project because we want you to be involved. We love issues, feature requests, code reviews, pullrequests or any positive contribution. Please see the the CONTRIBUTING guide for how to help, including how to build your own extension.
Highlighted Features
- AWSCLI - Interact with the AWSCLI (Windows hosts only)
- AWS Powershell Module - Interact with AWS through powershell (Windows hosts only)
- Beanstalk - Deploy ElasticBeanstalk applications
- CodeDeploy - Deploy with CodeDeploy
- CloudFormation - Create/Delete/Update CloudFormation stacks
- ECR - Push an image to an ECR repository
- Lambda - Deploy from S3, .net core applications, or any other language that builds on Azure DevOps
- S3 - Upload/Download to/from S3 buckets
- Secrets Manager - Create and retrieve secrets
- SQS - Send SQS messages
- SNS - Send SNS messages
- Systems manager - Get/set parameters and run commands
User Guide
The User Guide contains additional instructions for getting up and running with the extension.
Aws Toolkit Visual Studio For Mac Osx
NOTE: The user-guide source content that used to live in this folder has been moved to its own GitHub repository.
Credentials Handling for AWS Services
To enable tasks to call AWS services when run as part of your build or release pipelines AWS credentials need to have been configured for the tasks or be available in the host process for the build agent. Note that the credentials are used specifically by the tasks when run in a build agent process, they are not related to end-user logins to your Azure DevOps instance.
The AWS tasks support the following mechanisms for obtaining AWS credentials:
- One or more service endpoints, of type AWS, can be created and populated with AWS access and secret keys, and optionally data for Assumed Role credentials.
- Tasks reference the configured service endpoint instances by name as part of their configuration and pull the required credentials from the endpoint when run.
- Variables defined on the task or build.
- If tasks are not configured with the name of a service endpoint they will attempt to obtain credentials, and optionally region, from variables defined in the build environment. Thevariables are named AWS.AccessKeyID, AWS.SecretAccessKey and optionally AWS.SessionToken. To supply the ID of the region to make the call in, e.g. us-west-2, you can also use the variable AWS.Region. Optionally a role to assume can be specified by using the variable AWS.AssumeRoleArn. When assuming roles AWS.RoleSessionName (optional) and AWS.ExternalId (optional) can be provided in order to specify an identifier for the assumed role session and an external id to show in customers' accounts when assuming roles.
- Environment variables in the build agent's environment.
- If tasks are not configured with the name of a service endpoint, and credentials or region are not available from task variables, the tasks will attempt to obtain credentials, and optionally region, from standard environment variables in the build process environment. These variables are AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY and optionally AWS_SESSION_TOKEN. To supply the ID of the region to make the call in, e.g. us-west-2, you can also use the environment variable AWS_REGION.
- EC2 instance metadata, for build hosts running on EC2 instances.
- Both credential and region information can be automatically obtained from the instance metadata in this scenario.
Configuring an AWS Service Endpoint
To use AWS service endpoints add the AWS subscription(s) to use by opening the Account Administration screen (gear icon on the top-right of the screen) and then click on the Services Tab. Note that each Azure DevOps project is associated with its own set of credentials. Service endpoints are not shared across projects. You can associate a single service endpoint to be used with all AWS tasks in a build or multiple endpoints if you require.
Select the AWS endpoint type and provide the following parameters. Please refer to About Access Keys:
- A name used to refer to the credentials when configuring the AWS tasks
- AWS Access Key ID
- AWS Secret Access Key
Note We strongly suggest you use access and secret keys generated for an Identity and Access Management (IAM) user account. You can configure an IAM user account with permissions granting access to only the services and resources required to support the tasks you intend to use in your build and release definitions.
Tasks can also use assumed role credentials by adding the Amazon Resource name (ARN) of the role to be assumed and an optional identifier when configuring the endpoint. The access and secret keys specified will then be used to generate temporary credentials for the tasks when they are executed by the build agents. Temporary credentials are valid for up to 15 minutes by default. To enable a longer validity period you can set the 'aws.rolecredential.maxduration' variable on your build or release definition, specifying a validity period in seconds between 15 minutes (900 seconds) and 12 hours (43200 seconds).
Supported environments
- Azure DevOps
- Team Foundation Server 2015 Update 3 (or higher) (now called Azure DevOps Server)
Note for Team Foundation Server 2015 Users: Team Foundation Server 2015 users should download the extension from here. This temporary version contains the same tasks as the version in the marketplace but removes the support for extra fields in the AWS endpoint type to support Assume Role credentials. These fields, although marked optional, are unfortunately treated as required in TFS 2015 editions.
License
The project is licensed under the MIT license
Aws Toolkit For Vs Code
Contributors
We thank the following contributor(s) for this extension: Visual Studio ALM Rangers.
In this tutorial I'll create a Serverless AWS Lambda Web API using, AWS Toolkit along with Visual Studio 2017, which will help to write and deploy the API all from inside the Visual Studio interface.
Why the focus on AWS Toolkit?
I’ve been interested in AWS for a while and I’ve noticed they have recently promoted their .NET core services by providing .NET tools, webinars and tutorials. In the recent 2018 AWS summit in Chicago, they dedicated multiple topics to using their cloud for the development and the deployment of .NET applications. They touted “AWS loves .NET”, in a way to attract more .NET workshops to shift to AWS instead of using cloud services from their biggest competitor — Azure.
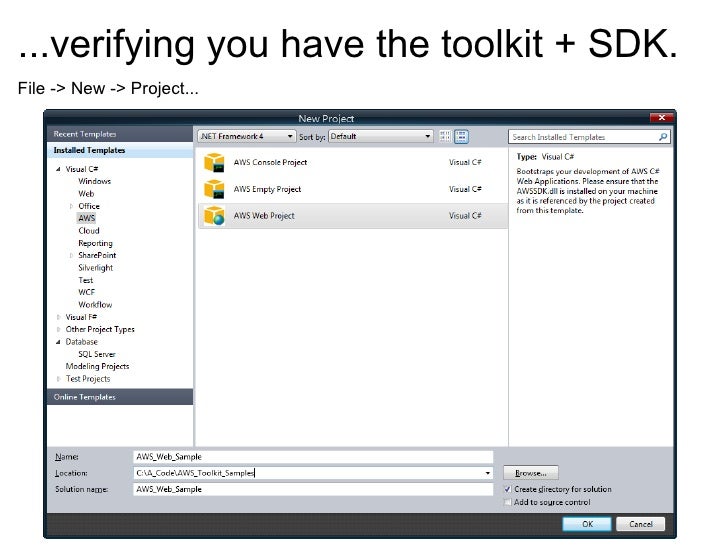
What is the AWS toolkit?
The AWS toolkit is a Visual Studio extension that supports 2013, 2015, and 2017 (only the Windows version, Mac version is not supported yet). This tool helps developers to create, debug, and publish applications to AWS all from Visual Studio. Such tasks can also be done using AWS console and they also have a similar AWS tool for Eclipse for other languages.
Let's create a simple Serverless .NET Core Web API with AWS Lambda to demonstrate using this tool in Visual Studio. We will also be using some other services such as S3 and IAM. We will hold off on discussing those details for now.
Creating a user
In order to set up and use the AWS Toolkit, create a user with administrator policy, then use this user’s access and secret keys to complete the setup.
Aws Tools For Visual Studio
Creating a user should be easy. After logging into AWS console, go to IAM then Users then click the “Add user” blue button. Then add the user information in 5 steps as below.
Step 3 is all about adding tags and more information to the account, and step 4 is a review page. Then you should be able to see the step 5 page, which has the access key as well as the secret key. Instead of copying these key, click the “download csv” button to get a csv file with the keys. Import the given csv file into the AWS toolkit later inside Visual Studio.
Installing the AWS Toolkit
The tool is available either through the AWS website or the Visual Studio Marketplace as an extension. You’ll be installing it that way. Under “Tools” -> “Extensions and updates” and then search for “AWS Toolkit” in the online extensions list, it should be right in the top. Click download. This might request you to restart Visual Studio to finish the installation.
After restarting Visual Studio, you'll be greeted by the AWS Toolkit welcome screen where the user’s access and secret keys should be added. In this case, click “Import from csv file” and that will take care of adding both of the keys. Finally, click the “Save and Close” yellow button.
Aws Toolkit For Visual Studio For Mac
Aws Toolkit For Visual Studio Code Mac
In our next tutorial, we'll create the AWS Lambda project.
